* fix(login): add loginname as query param, send with inituserlink * set loginname as username autofill on password site * add loginname input on change password * fix console password change autocomplete * fix(console): apply labelpolicy if icon is provided, signout page (#4499) * label policy as observable * signedout policy via state * add caching * disable loading spinner on signedout * cleanup * catch error * update deps * move policy to localstorage * handle labelpolicy for users without org Co-authored-by: Livio Spring <livio.a@gmail.com> Co-authored-by: Fabi <38692350+hifabienne@users.noreply.github.com> * fix(email): set sender address as return-path header (#4569) * feat(login): additionally use email/phone for authentication (#4563) * feat: add ability to disable login by email and phone * feat: check login by email and phone * fix: set verified email / phone correctly on notify users * update projection version * fix merge * fix email/phone verified reduce tests * fix user tests * loginname check * cleanup * fix: update user projection version to handle fixed statement * ci(e2e): give console init time (#4567) * fix: idp usage (#4571) * fix: send email verification instead of init code for idp users * fix: select single idp of external only users * fix: use single idp on login * fix(import): add import for app and machine keys (#4536) * fix(import): add import for app and machine keys * fix(export): add review changes * fix(import): Apply suggestions from code review Co-authored-by: Livio Spring <livio.a@gmail.com> * fix(import): add review changes Co-authored-by: Livio Spring <livio.a@gmail.com> * fix(console): hide metadata on auth side if no `user.read` role present (#4512) * check for role * require user.read for showing metadata section in auth-user * remove aggregate id from role check Co-authored-by: Livio Spring <livio.a@gmail.com> * update stable release to 2.8.2 (#4574) * fix: import of trigger actions and export of idp links (#4576) Co-authored-by: Livio Spring <livio.a@gmail.com> * fix(console): split password from contact information, initialization mail on top (#4380) * chore(console): split password from contact information * change user detail, initialization mail * fix translation * Update console/src/assets/i18n/de.json Co-authored-by: Elio Bischof <eliobischof@gmail.com> * Update console/src/assets/i18n/de.json Co-authored-by: Elio Bischof <eliobischof@gmail.com> * Update console/src/assets/i18n/en.json Co-authored-by: Elio Bischof <eliobischof@gmail.com> * Update console/src/assets/i18n/fr.json Co-authored-by: Elio Bischof <eliobischof@gmail.com> * Update console/src/assets/i18n/fr.json Co-authored-by: Elio Bischof <eliobischof@gmail.com> * Update console/src/assets/i18n/it.json Co-authored-by: Elio Bischof <eliobischof@gmail.com> * Update console/src/assets/i18n/en.json Co-authored-by: Elio Bischof <eliobischof@gmail.com> * i18n Co-authored-by: Elio Bischof <eliobischof@gmail.com> * fix(import): import json marshal to jsonpb (#4580) * fix(import): import json marshal to jsonpb * fix: add unmarshaloptions discard unknown Co-authored-by: Livio Spring <livio.a@gmail.com> * fix(import): import json marshal to jsonpb Co-authored-by: Livio Spring <livio.a@gmail.com> * feat(console): rename org (#4542) * rename org * add data-e2e * e2e test * restore state after * use ngIf instead of hasrole directive and initialized regex * rm h2 check * Update e2e/cypress/e2e/organization/organizations.cy.ts Co-authored-by: Elio Bischof <eliobischof@gmail.com> * Update console/src/assets/i18n/de.json Co-authored-by: Elio Bischof <eliobischof@gmail.com> * Update console/src/assets/i18n/de.json Co-authored-by: Elio Bischof <eliobischof@gmail.com> * Update console/src/assets/i18n/en.json Co-authored-by: Elio Bischof <eliobischof@gmail.com> * change e2e test * org param * reintroduct org param * use org query param * org rename test * no initial focus on button * contain name Co-authored-by: Elio Bischof <eliobischof@gmail.com> * feat: instance remove (#4345) * feat(instance): add remove instance event with projections cleanup * fix(instance): corrected used id to clean up projections * fix merge * fix: correct unit test projection names * fix: current sequence of lists and query for ensuring keypair based projections Co-authored-by: Livio Spring <livio.a@gmail.com> Co-authored-by: Fabi <38692350+hifabienne@users.noreply.github.com> * docs: change nextjs quickstart (#4566) * docs: change nextjs repo update readme * Update docs/docs/examples/login/nextjs.md Co-authored-by: Florian Forster <florian@zitadel.com> * Update docs/docs/examples/login/nextjs.md Co-authored-by: Florian Forster <florian@zitadel.com> Co-authored-by: Florian Forster <florian@zitadel.com> * fix(console): preserve logo and icon aspect ratios, remove border radius in header (#4585) * chore(e2e): Skip asking for new password on Admin in dev environment (#4599) * feat(e2e): Skip asking for new password on Admin * remove password changing Co-authored-by: Elio Bischof <eliobischof@gmail.com> * docs(contributing): remove guides folder (#4603) * preferredLoginName as queryParam Co-authored-by: Fabi <38692350+hifabienne@users.noreply.github.com> Co-authored-by: Livio Spring <livio.a@gmail.com> Co-authored-by: Elio Bischof <eliobischof@gmail.com> Co-authored-by: Stefan Benz <46600784+stebenz@users.noreply.github.com> Co-authored-by: Florian Forster <florian@zitadel.com> Co-authored-by: p_0g_8mm3_ <37022952+pr0gr8mm3r@users.noreply.github.com>
You want auth that's quickly set up like Auth0 but open source like Keycloak? Look no further — ZITADEL combines the ease of Auth0 and the versatility of Keycloak.
We provide a wide range of out of the box features like secure login, self-service, OpenID Connect, OAuth2.x, SAML2, branding, Passwordless with FIDO2, OTP, U2F, and an unlimited audit trail to improve the life of developers. Especially noteworthy is that ZITADEL supports not only B2C and B2E scenarios but also B2B. This is super useful for people who build B2B Solutions, as ZITADEL can handle all the delegated user and access management.
With ZITADEL you rely on a battle tested, hardened and extensible turnkey solution to solve all of your authentication and authorization needs. With the unique way of how ZITADEL stores data it gives you an unlimited audit trail which provides a peace of mind for even the harshest audit and analytics requirements.
🏡 Website 💬 Chat 📋 Docs 🧑💻 Blog 📞 Contact
Get started
ZITADEL Cloud (SaaS)
The easiest way to get started with ZITADEL Cloud.
It's free for up to 25'000 authenticated requests. Learn more about the pay-as-you-go pricing.
Install ZITADEL
Quickstarts - Integrate your app
Multiple Examples can be found here
If you miss something please feel free to join the Discussion
Why ZITADEL
- API-first
- Strong audit trail thanks to event sourcing
- Actions to react on events with custom code
- Branding for a uniform user experience
- CockroachDB or a Postgres database is the only dependency
Features
- Single Sign On (SSO)
- Passwordless with FIDO2 support
- Username / Password
- Multifactor authentication with OTP, U2F
- Identity Brokering
- Machine-to-machine (JWT profile)
- Personal Access Tokens (PAT)
- Role Based Access Control (RBAC)
- Delegate role management to third-parties
- Self-registration including verification
- User self service
- Service Accounts
- OpenID Connect certified => OIDC Endpoints, OIDC Integration Guides
- SAML 2.0 => SAML Endpoints, SAML Integration Guides
- Postgres (version >= 14) or CockroachDB (version >= 22.0)
Track upcoming features on our roadmap.
Client libraries
| Language | Client | API | Machine auth (*) | Auth check (**) | Thanks to the maintainers |
|---|---|---|---|---|---|
| .NET | zitadel-net | GRPC | ✔️ | ✔️ | smartive 👑 |
| Dart | zitadel-dart | GRPC | ✔️ | ❌ | smartive 👑 |
| Elixir | zitadel_api | GRPC | ✔️ | ✔️ | jshmrtn 🙏🏻 |
| Go | zitadel-go | GRPC | ✔️ | ✔️ | ZITADEL |
| Rust | zitadel-rust | GRPC | ✔️ | ❌ | smartive 👑 |
| JVM | 🚧 WIP | ❓ | ❓ | TBD | |
| Python | 🚧 WIP | ❓ | ❓ | TBD | |
| Javascript | ❓ | ❓ | ❓ | Maybe you? |
(*) Automatically authenticate service accounts with JWT Profile.
(**) Automatically check if the access token is valid and claims match
How To Contribute
Details about how to contribute you can find in the Contribution Guide
Contributors
Made with contrib.rocks.
Showcase
Passwordless Login
Use our login widget to allow easy and secure access to your applications and enjoy all the benefits of passwordless (FIDO 2 / WebAuthN):
- works on all modern platforms, devices, and browsers
- phishing resistant alternative
- requires only one gesture by the user
- easy enrollment of the device during registration
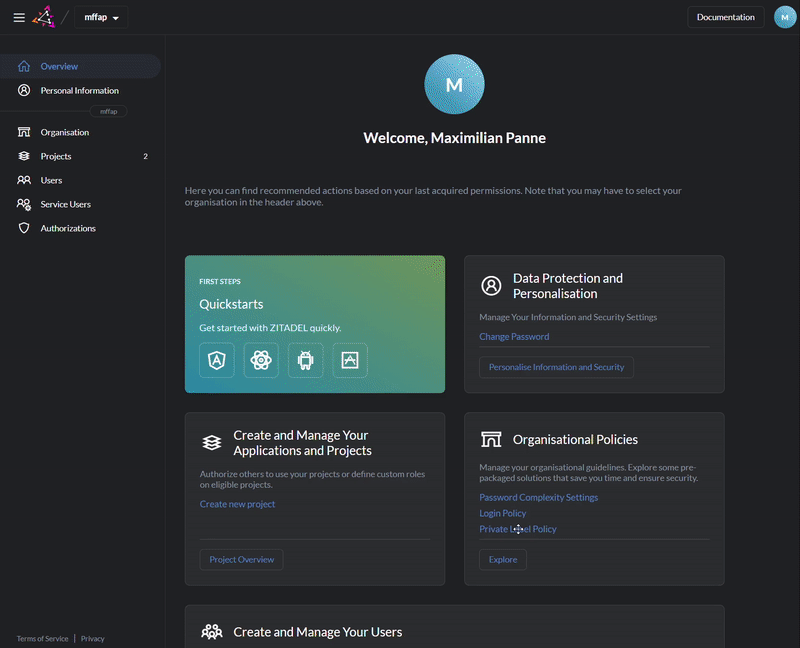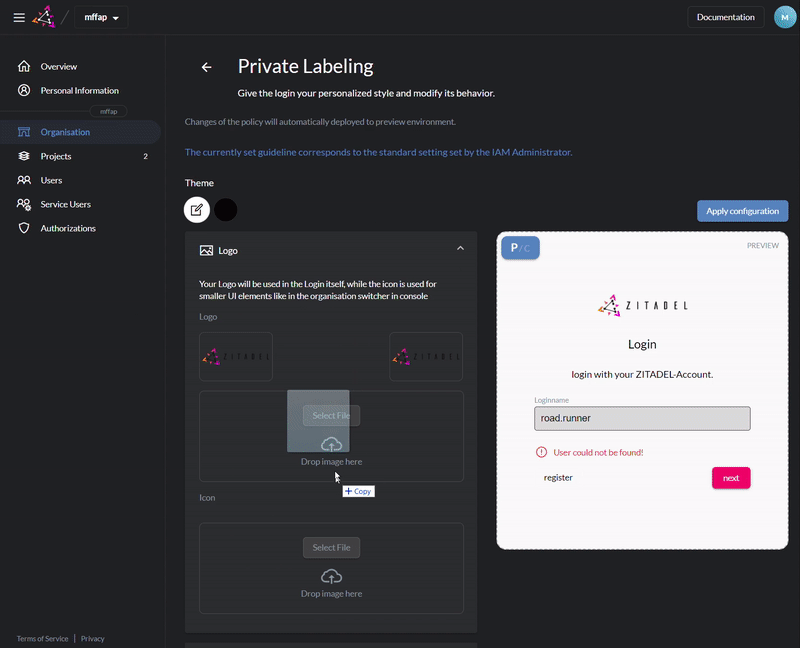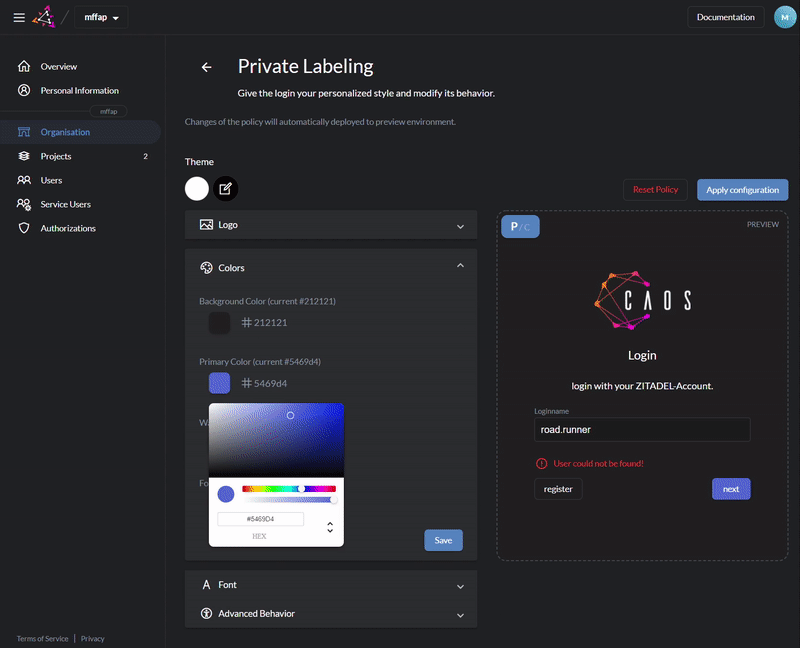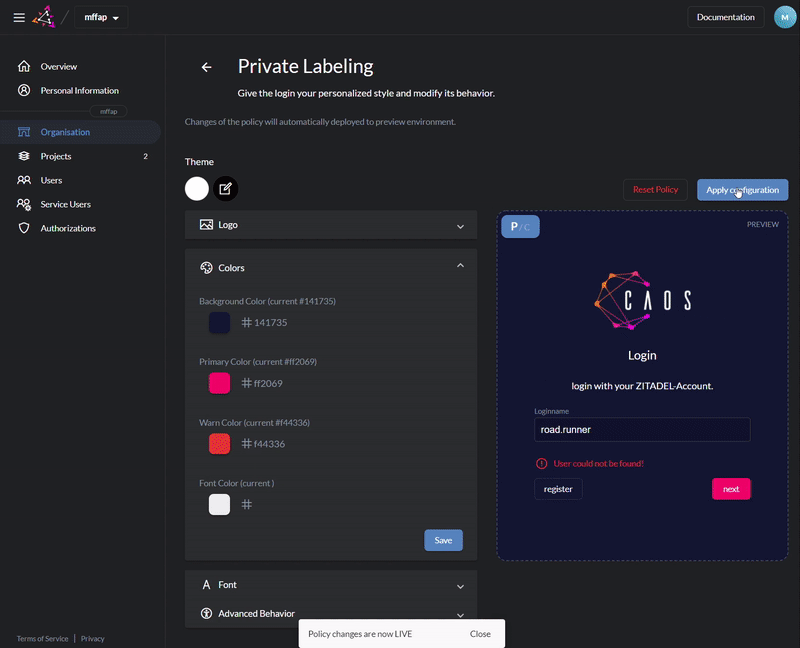
Admin Console
Use Console or our APIs to setup organizations, projects and applications.
Delegate the right to assign roles to another organization

Customize login and console with your design
Security
See the policy here
License
See the exact licensing terms here
Unless required by applicable law or agreed to in writing, software distributed under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. See the License for the specific language governing permissions and limitations under the License.