# Which Problems Are Solved
1. The projection handler reported no error if an error happened but
updating the current state was successful. This can lead to skipped
projections during setup as soon as the projection has an error but does
not correctly report if to the caller.
2. Mirror projections skipped as soon as an error occures, this leads to
unprojected projections.
3. Mirror checked position wrongly in some cases
# How the Problems Are Solved
1. the error returned by the `Trigger` method will will only be set to
the error of updating current states if there occured an error.
2. triggering projections checks for the error type returned and retries
if the error had code `23505`
3. Corrected to use the `Equal` method
# Additional Changes
unify logging on mirror projections
# Which Problems Are Solved
1. After second execution, mirror starts to fail because of Primary key
constraints on the events table. Because mirror always took the the
first `system.mirror.succeeded` instead of the newest one
2. Mirror panicked during migration of fields tables
# How the Problems Are Solved
1. Adjusted the database query to order descending and limit 1
2. added missing assignment
# Additional Changes
- detailed logging if the copy from statement failed.
# Which Problems Are Solved
- fields projections were not projected during mirror
# How the Problems Are Solved
- an extra step during projections was added to mirror the fields
# Additional Changes
none
# Additional Context
none
# Which Problems Are Solved
Float64 which was used for the event.Position field is [not precise in
go and gets rounded](https://github.com/golang/go/issues/47300). This
can lead to unprecies position tracking of events and therefore
projections especially on cockcoachdb as the position used there is a
big number.
example of a unprecies position:
exact: 1725257931223002628
float64: 1725257931223002624.000000
# How the Problems Are Solved
The float64 was replaced by
[github.com/jackc/pgx-shopspring-decimal](https://github.com/jackc/pgx-shopspring-decimal).
# Additional Changes
Rename `latestSequence`-queries to `latestPosition`
# Additional Context
closes https://github.com/zitadel/zitadel/issues/8863
# Which Problems Are Solved
During the mirror command execution we saw high wait times for
notification projections.
# How the Problems Are Solved
As the events are skipped anyways because the notifications are sent out
by the source Zitadel we skip the projections and just set the current
state.
The `auth.auth_requests` table is not cleaned up so long running Zitadel
installations can contain many rows.
The mirror command can take long because a the data are first copied
into memory (or disk) on cockroach and users do not get any output from
mirror. This is unfortunate because people don't know if Zitadel got
stuck.
Enhance logging throughout the projection processes and introduce a
configuration option for the maximum age of authentication requests.
None
closes https://github.com/zitadel/zitadel/issues/9764
---------
Co-authored-by: Livio Spring <livio.a@gmail.com>
# Which Problems Are Solved
E2E tests in pipelines started to fail randomly. While debugging it, i
noticed that we use the `latest` tag of cockroach's docker image. They
tagged 25.1 as latest yesterday.
# How the Problems Are Solved
Since we drop support for CRDB with version 3 as there are anyway
multiple issues with various versions, I pinned the docker image tag to
`latest-v24.3`.
# Additional Changes
None
# Additional Context
relates to https://github.com/zitadel/zitadel/actions/runs/13917603587
and https://github.com/zitadel/zitadel/actions/runs/13904928050
(cherry picked from commit f1f500d0e7)
# Which Problems Are Solved
ZITADEL allows the use of JSON Web Token (JWT) Profile OAuth 2.0 for Authorization Grants in machine-to-machine (M2M) authentication. Multiple keys can be managed for a single machine account (service user), each with an individual expiry.
A vulnerability existed where expired keys can be used to retrieve tokens. Specifically, ZITADEL fails to properly check the expiration date of the JWT key when used for Authorization Grants. This allows an attacker with an expired key to obtain valid access tokens.
This vulnerability does not affect the use of JWT Profile for OAuth 2.0 Client Authentication on the Token and Introspection endpoints, which correctly reject expired keys.
# How the Problems Are Solved
Added proper validation of the expiry of the stored public key.
# Additional Changes
None
# Additional Context
None
(cherry picked from commit 315503beab)
# Which Problems Are Solved
The username entered by the user was resp. replaced by the stored user's username. This provided a possibility to enumerate usernames as unknown usernames were not normalized.
# How the Problems Are Solved
- Store and display the username as entered by the user.
- Removed the part where the loginname was always set to the user's loginname when retrieving the `nextSteps`
# Additional Changes
None
# Additional Context
None
(cherry picked from commit 14de8ecac2)
# Which Problems Are Solved
ZITADEL's Admin API, intended for managing ZITADEL instances, contains 12 HTTP endpoints that are unexpectedly accessible to authenticated ZITADEL users who are not ZITADEL managers. The most critical vulnerable endpoints relate to LDAP configuration:
- /idps/ldap
- /idps/ldap/{id}
By accessing these endpoints, unauthorized users could:
- Modify ZITADEL's instance LDAP settings, redirecting all LDAP login attempts to a malicious server, effectively taking over user accounts.
- Expose the original LDAP server's password, potentially compromising all user accounts.
The following endpoints are also affected by IDOR vulnerabilities, potentially allowing unauthorized modification of instance settings such as languages, labels, and templates:
- /idps/templates/_search
- /idps/templates/{id}
- /policies/label/_activate
- /policies/label/logo
- /policies/label/logo_dark
- /policies/label/icon
- /policies/label/icon_dark
- /policies/label/font
- /text/message/passwordless_registration/{language}
- /text/login/{language}
Please checkout https://github.com/zitadel/zitadel/security/advisories/GHSA-f3gh-529w-v32x for more information.
# How the Problems Are Solved
- Required permission have been fixed (only instance level allowed)
# Additional Changes
None
# Additional Context
- resolves https://github.com/zitadel/zitadel/security/advisories/GHSA-f3gh-529w-v32x
(cherry picked from commit d9d8339813)
# Which Problems Are Solved
During authentication in the login UI, there is a check if the user's
MFA is already checked or needs to be setup.
In cases where the user was just set up or especially, if the user was
just federated without a verified email address, this can lead to the
problem, where OTP Email cannot be setup as there's no verified email
address.
# How the Problems Are Solved
- Added a check if there's no verified email address on the user and
require a mail verification check before checking for MFA.
Note: that if the user had a verified email address, but changed it and
has not verified it, they will still be prompted with an MFA check
before the email verification. This is make sure, we don't break the
existing behavior and the user's authentication is properly checked.
# Additional Changes
None
# Additional Context
- closes https://github.com/zitadel/zitadel/issues/9035
(cherry picked from commit f20539ef8f)
# Which Problems Are Solved
The `CreateInviteCode` and `VerifyInviteCode` methods missed the body
mapping.
# How the Problems Are Solved
Added the mapping.
# Additional Changes
None
# Additional Context
Noticed during internal login UI tests using REST
(cherry picked from commit fd70a7de5f)
# Which Problems Are Solved
Slice initialized with a fixed length instead of capacity, this leads to
unexpected results when calling the append function.
# How the Problems Are Solved
fixed slice initialization, slice is initialized with zero length and
with capacity of function's argument
# Additional Changes
test case added
# Additional Context
none
Co-authored-by: Kolokhanin Roman <zuzmic@gmail.com>
Co-authored-by: Tim Möhlmann <tim+github@zitadel.com>
(cherry picked from commit d0c23546ec)
# Which Problems Are Solved
Wrongly created project grants with a unexpected resourceowner can't be
removed as there is a check if the project is existing, the project is
never existing as the wrong resourceowner is used.
# How the Problems Are Solved
There is already a fix related to the resourceowner of the project
grant, which should remove the possibility that this situation can
happen anymore. This PR removes the check for the project existing, as
when the projectgrant is existing and the project is not already
removed, this check is not needed anymore.
# Additional Changes
None
# Additional Context
Closes#8900
(cherry picked from commit 14db628856)
# Which Problems Are Solved
Noisy neighbours can introduce projection latencies because the
projections only query events older than the start timestamp of the
oldest push transaction.
# How the Problems Are Solved
During push we set the application name to
`zitadel_es_pusher_<instance_id>` instead of `zitadel_es_pusher` which
is used to query events by projections.
(cherry picked from commit 522c82876f)
# Which Problems Are Solved
There are multiple issues with the metadata and error handling of SAML:
- When providing a SAML metadata for an IdP, which cannot be processed,
the error will only be noticed once a user tries to use the IdP.
- Parsing for metadata with any other encoding than UTF-8 fails.
- Metadata containing an enclosing EntitiesDescriptor around
EntityDescriptor cannot be parsed.
- Metadata's `validUntil` value is always set to 48 hours, which causes
issues on external providers, if processed from a manual down/upload.
- If a SAML response cannot be parsed, only a generic "Authentication
failed" error is returned, the cause is hidden to the user and also to
actions.
# How the Problems Are Solved
- Return parsing errors after create / update and retrieval of an IdP in
the API.
- Prevent the creation and update of an IdP in case of a parsing
failure.
- Added decoders for encodings other than UTF-8 (including ASCII,
windows and ISO, [currently
supported](efd25daf28/encoding/ianaindex/ianaindex.go (L156)))
- Updated parsing to handle both `EntitiesDescriptor` and
`EntityDescriptor` as root element
- `validUntil` will automatically set to the certificate's expiration
time
- Unwrapped the hidden error to be returned. The Login UI will still
only provide a mostly generic error, but action can now access the
underlying error.
# Additional Changes
None
# Additional Context
reported by a customer
(cherry picked from commit ffe9570776)
# Which Problems Are Solved
- ImportHuman was not checking for a `UserStateDeleted` state on import,
resulting in "already existing" errors when attempting to delete and
re-import a user with the same id
# How the Problems Are Solved
Use the `Exists` helper method to check for both `UserStateUnspecified`
and `UserStateDeleted` states on import
# Additional Changes
N/A
# Additional Context
N/A
Co-authored-by: Livio Spring <livio.a@gmail.com>
(cherry picked from commit 7ba797b872)
# Which Problems Are Solved
Some SAML IdPs including Google only allow to configure a single
AssertionConsumerService URL.
Since the current metadata provides multiple and the hosted login UI is
not published as neither the first nor with `isDefault=true`, those IdPs
take another and then return an error on sign in.
# How the Problems Are Solved
Allow to reorder the ACS URLs using a query parameter
(`internalUI=true`) when retrieving the metadata endpoint.
This will list the `ui/login/login/externalidp/saml/acs` first and also
set the `isDefault=true`.
# Additional Changes
None
# Additional Context
Reported by a customer
(cherry picked from commit 374b9a7f66)
# Which Problems Are Solved
The order of actions on a trigger was not respected on the execution and
not correctly returned when retrieving the flow, for example in Console.
The supposed correction of the order (e.g. in the UI) would then return
a "no changes" error since the order was already as desired.
# How the Problems Are Solved
- Correctly order the actions of a trigger based on their configuration
(`trigger_sequence`).
# Additional Changes
- replaced a `reflect.DeepEqual` with `slices.Equal` for checking the
action list
# Additional Context
- reported by a customer
- requires backports
(cherry picked from commit 85bdf01505)
# Which Problems Are Solved
By having default entries in the `Username` and `ClientName` fields, it
was not possible to unset there parameters. Unsetting them is required
for GCP connections
# How the Problems Are Solved
Set the fields to empty strings.
# Additional Changes
- none
# Additional Context
- none
(cherry picked from commit b77901cb4b)
# Which Problems Are Solved
The setup filter for previous steps and kept getting slower. This is due
to the filter, which did not provide any instanceID and thus resulting
in a full table scan.
# How the Problems Are Solved
- Added an empty instanceID filter (since it's on system level)
# Additional Changes
None
# Additional Context
Noticed internally and during migrations on some regions
(cherry picked from commit ecbf0db15b)
# Which Problems Are Solved
Fixes 'column "instance_id" does not exist' errors from #8558.
# How the Problems Are Solved
The instanceClause / WHERE clause in the query for the respective tables
is excluded.
I have successfully created a mirror with this change.
(cherry picked from commit a09c772b03)
# Which Problems Are Solved
Do not return an access token for implicit flow from v1 login, if the
`response_type` is `id_token`
# How the Problems Are Solved
Do not create the access token event if if the `response_type` is
`id_token`.
# Additional Changes
Token endpoint calls without auth request, such as machine users, token
exchange and refresh token, do not have a `response_type`. For such
calls the `OIDCResponseTypeUnspecified` enum is added at a `-1` offset,
in order not to break existing client configs.
# Additional Context
- https://discord.com/channels/927474939156643850/1294001717725237298
- Fixes https://github.com/zitadel/zitadel/issues/8776
(cherry picked from commit 778b4041ca)
# Which Problems Are Solved
The intention here should be to initialize a slice with a capacity of
len(queriedOrgs.Orgs) rather than initializing the length of this slice.
the online demo: https://go.dev/play/p/vNUPNjdb2gJ
# How the Problems Are Solved
use `processedOrgs := make([]string, 0, len(queriedOrgs.Orgs))`
# Additional Changes
None
# Additional Context
None
Co-authored-by: Tim Möhlmann <tim+github@zitadel.com>
(cherry picked from commit 69e9926bcc)
# Which Problems Are Solved
https://github.com/zitadel/zitadel/pull/8788 accidentally changed the
spelling of milestone types from PascalCase to snake_case. This breaks
systems where `milestone.pushed` events already exist.
# How the Problems Are Solved
- Use PascalCase again
- Prefix event types with v2. (Previous pushed event type was anyway
ignored).
- Create `milstones3` projection
# Additional Changes
None
# Additional Context
relates to #8788
# Which Problems Are Solved
Add a cache implementation using Redis single mode. This does not add
support for Redis Cluster or sentinel.
# How the Problems Are Solved
Added the `internal/cache/redis` package. All operations occur
atomically, including setting of secondary indexes, using LUA scripts
where needed.
The [`miniredis`](https://github.com/alicebob/miniredis) package is used
to run unit tests.
# Additional Changes
- Move connector code to `internal/cache/connector/...` and remove
duplicate code from `query` and `command` packages.
- Fix a missed invalidation on the restrictions projection
# Additional Context
Closes#8130
# Which Problems Are Solved
Currently ZITADEL supports RP-initiated logout for clients. Back-channel
logout ensures that user sessions are terminated across all connected
applications, even if the user closes their browser or loses
connectivity providing a more secure alternative for certain use cases.
# How the Problems Are Solved
If the feature is activated and the client used for the authentication
has a back_channel_logout_uri configured, a
`session_logout.back_channel` will be registered. Once a user terminates
their session, a (notification) handler will send a SET (form POST) to
the registered uri containing a logout_token (with the user's ID and
session ID).
- A new feature "back_channel_logout" is added on system and instance
level
- A `back_channel_logout_uri` can be managed on OIDC applications
- Added a `session_logout` aggregate to register and inform about sent
`back_channel` notifications
- Added a `SecurityEventToken` channel and `Form`message type in the
notification handlers
- Added `TriggeredAtOrigin` fields to `HumanSignedOut` and
`TerminateSession` events for notification handling
- Exported various functions and types in the `oidc` package to be able
to reuse for token signing in the back_channel notifier.
- To prevent that current existing session termination events will be
handled, a setup step is added to set the `current_states` for the
`projections.notifications_back_channel_logout` to the current position
- [x] requires https://github.com/zitadel/oidc/pull/671
# Additional Changes
- Updated all OTEL dependencies to v1.29.0, since OIDC already updated
some of them to that version.
- Single Session Termination feature is correctly checked (fixed feature
mapping)
# Additional Context
- closes https://github.com/zitadel/zitadel/issues/8467
- TODO:
- Documentation
- UI to be done: https://github.com/zitadel/zitadel/issues/8469
---------
Co-authored-by: Hidde Wieringa <hidde@hiddewieringa.nl>
# Which Problems Are Solved
Migration of milestones failed on our QA due to the new milestone Type
enum being 0-indexed. The valid range was 0 till 5, inclusive. While on
the previous zitadel version this was 1 till 6, inclusive.
# How the Problems Are Solved
Offset the first constant with `1`.
# Additional Changes
- none
# Additional Context
Introduced in https://github.com/zitadel/zitadel/pull/8788
ZITADEL CI/CD / core-unit-test (push) Has been skipped
ZITADEL CI/CD / core-integration-test (push) Has been skipped
ZITADEL CI/CD / console (push) Failing after 9m42s
ZITADEL CI/CD / lint (push) Has been skipped
ZITADEL CI/CD / version (push) Successful in 11m8s
ZITADEL CI/CD / compile (push) Has been skipped
ZITADEL CI/CD / container (push) Has been skipped
ZITADEL CI/CD / e2e (push) Has been skipped
ZITADEL CI/CD / release (push) Has been skipped
# Which Problems Are Solved
As we switched to PostgreSQL with our cloud zitadel, we now want to
recommend it instead of CockroachDB.
# How the Problems Are Solved
Replaced the recommend section with postgresql
ZITADEL CI/CD / compile (push) Blocked by required conditions
ZITADEL CI/CD / core-unit-test (push) Blocked by required conditions
ZITADEL CI/CD / core-integration-test (push) Blocked by required conditions
ZITADEL CI/CD / lint (push) Blocked by required conditions
ZITADEL CI/CD / container (push) Blocked by required conditions
ZITADEL CI/CD / e2e (push) Blocked by required conditions
ZITADEL CI/CD / release (push) Blocked by required conditions
Code Scanning / CodeQL-Build (javascript) (push) Failing after 7m42s
Code Scanning / CodeQL-Build (go) (push) Failing after 15m0s
# Which Problems Are Solved
Resource owner can be different than expected if the provided
x-zitadel-orgid header is provided.
# How the Problems Are Solved
Check that the project is only checked with the correct resource owner
to avoid unexpected situations.
# Additional Changes
None
# Additional Context
Closes#8685
---------
Co-authored-by: Livio Spring <livio.a@gmail.com>
ZITADEL CI/CD / compile (push) Blocked by required conditions
ZITADEL CI/CD / core-unit-test (push) Blocked by required conditions
ZITADEL CI/CD / core-integration-test (push) Blocked by required conditions
ZITADEL CI/CD / lint (push) Blocked by required conditions
ZITADEL CI/CD / container (push) Blocked by required conditions
ZITADEL CI/CD / e2e (push) Blocked by required conditions
ZITADEL CI/CD / release (push) Blocked by required conditions
Code Scanning / CodeQL-Build (go) (push) Waiting to run
Code Scanning / CodeQL-Build (javascript) (push) Waiting to run
# Which Problems Are Solved
1. Postgres spams FATAL: role "root" does not exist as mentioned in
https://github.com/zitadel/zitadel/discussions/7832 (even with -U)
2. The compose commands for a ZITADEL deployment with initial service
account key don't work out-of-the box with a non-root user, because
docker creates non-existing directories to bind-mount with root
ownership.
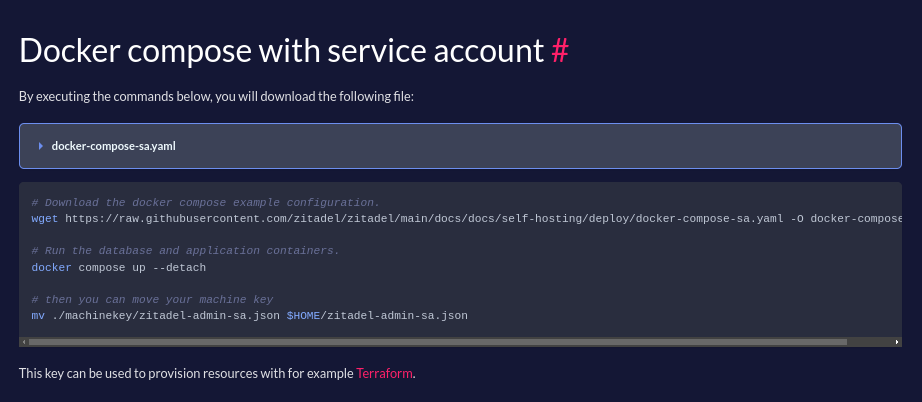
```
time="2024-10-29T09:37:13Z" level=error msg="migration failed" caller="/home/runner/work/zitadel/zitadel/internal/migration/migration.go:68" error="open /machinekey/zitadel-admin-sa.json: permission denied" name=03_default_instance
time="2024-10-29T09:37:13Z" level=fatal msg="migration failed" caller="/home/runner/work/zitadel/zitadel/cmd/setup/setup.go:248" error="open /machinekey/zitadel-admin-sa.json: permission denied" name=03_default_instance
```
# How the Problems Are Solved
1. The branch bases on https://github.com/zitadel/zitadel/pull/8826. The
env vars are cleaned up and prettified across compose files.
2. A command is added to the docs that creates the directory with the
current users permission. The ZITADEL container runs with the current
users ID.
# Additional Context
- Replaces https://github.com/zitadel/zitadel/pull/8826
- Discussion https://github.com/zitadel/zitadel/discussions/7832
- Closes https://github.com/zitadel/zitadel/issues/7725
---------
Co-authored-by: m4tu4g <71326926+m4tu4g@users.noreply.github.com>
Code Scanning / CodeQL-Build (go) (push) Has been cancelled
Code Scanning / CodeQL-Build (javascript) (push) Has been cancelled
ZITADEL CI/CD / compile (push) Has been cancelled
ZITADEL CI/CD / core-unit-test (push) Has been cancelled
ZITADEL CI/CD / core-integration-test (push) Has been cancelled
ZITADEL CI/CD / lint (push) Has been cancelled
ZITADEL CI/CD / container (push) Has been cancelled
ZITADEL CI/CD / e2e (push) Has been cancelled
ZITADEL CI/CD / release (push) Has been cancelled
# Which Problems Are Solved
Closes: #8757
Problem:
```sh
➜ ~ date --rfc-3339=seconds | sed 's/ /T/'
date: illegal option -- -
usage: date [-jnRu] [-I[date|hours|minutes|seconds]] [-f input_fmt]
[-r filename|seconds] [-v[+|-]val[y|m|w|d|H|M|S]]
[[[[mm]dd]HH]MM[[cc]yy][.SS] | new_date] [+output_fmt]
```
# How the Problems Are Solved
```sh
➜ date "+%Y-%m-%dT%T%z" | sed -E 's/.([0-9]{2})([0-9]{2})$/-\1:\2/'
2024-10-10T19:09:53-05:30
➜ TZ=America/Los_Angeles date "+%Y-%m-%dT%T%z" | sed -E 's/.([0-9]{2})([0-9]{2})$/-\1:\2/'
2024-10-10T06:39:41-07:00
```
- `Mac` support while compiling the source code locally
Co-authored-by: Stefan Benz <46600784+stebenz@users.noreply.github.com>
ZITADEL CI/CD / compile (push) Blocked by required conditions
ZITADEL CI/CD / core-unit-test (push) Blocked by required conditions
ZITADEL CI/CD / core-integration-test (push) Blocked by required conditions
ZITADEL CI/CD / lint (push) Blocked by required conditions
ZITADEL CI/CD / container (push) Blocked by required conditions
ZITADEL CI/CD / e2e (push) Blocked by required conditions
ZITADEL CI/CD / release (push) Blocked by required conditions
Code Scanning / CodeQL-Build (go) (push) Waiting to run
Code Scanning / CodeQL-Build (javascript) (push) Waiting to run
# Which Problems Are Solved
Milestones used existing events from a number of aggregates. OIDC
session is one of them. We noticed in load-tests that the reduction of
the oidc_session.added event into the milestone projection is a costly
business with payload based conditionals. A milestone is reached once,
but even then we remain subscribed to the OIDC events. This requires the
projections.current_states to be updated continuously.
# How the Problems Are Solved
The milestone creation is refactored to use dedicated events instead.
The command side decides when a milestone is reached and creates the
reached event once for each milestone when required.
# Additional Changes
In order to prevent reached milestones being created twice, a migration
script is provided. When the old `projections.milestones` table exist,
the state is read from there and `v2` milestone aggregate events are
created, with the original reached and pushed dates.
# Additional Context
- Closes https://github.com/zitadel/zitadel/issues/8800
# Which Problems Are Solved
Searching orgs by domain currently only looked for the primary domain,
but should be possible with all verified domains (as documented)
# How the Problems Are Solved
- fixed the search query
# Additional Changes
None
# Additional Context
- closes https://github.com/zitadel/zitadel/issues/8749
ZITADEL CI/CD / compile (push) Blocked by required conditions
ZITADEL CI/CD / core-unit-test (push) Blocked by required conditions
ZITADEL CI/CD / core-integration-test (push) Blocked by required conditions
ZITADEL CI/CD / lint (push) Blocked by required conditions
ZITADEL CI/CD / container (push) Blocked by required conditions
ZITADEL CI/CD / e2e (push) Blocked by required conditions
ZITADEL CI/CD / release (push) Blocked by required conditions
Code Scanning / CodeQL-Build (go) (push) Waiting to run
Code Scanning / CodeQL-Build (javascript) (push) Waiting to run
# Which Problems Are Solved
Previously, the login lifetime input fields allowed negative values and,
in some cases, zero values, which were not valid according to the
business rules.
# How the Problems Are Solved
The issue was resolved by adding min and step properties to the relevant
HTML input fields. This ensures that only valid values are entered,
adhering to the specific requirements for each field.
Co-authored-by: Max Peintner <max@caos.ch>
Code Scanning / CodeQL-Build (go) (push) Has been cancelled
Code Scanning / CodeQL-Build (javascript) (push) Has been cancelled
ZITADEL CI/CD / compile (push) Has been cancelled
ZITADEL CI/CD / core-unit-test (push) Has been cancelled
ZITADEL CI/CD / core-integration-test (push) Has been cancelled
ZITADEL CI/CD / lint (push) Has been cancelled
ZITADEL CI/CD / container (push) Has been cancelled
ZITADEL CI/CD / e2e (push) Has been cancelled
ZITADEL CI/CD / release (push) Has been cancelled
# Which Problems Are Solved
In integration tests there is waiting for the application, but the
project is also included if the token can be created.
# How the Problems Are Solved
Wait for project not only for the application in the integration tests.
# Additional Changes
Some more corrections in integration tests.
# Additional Context
None
---------
Co-authored-by: Livio Spring <livio.a@gmail.com>