* variable parser * rm plugin * set fcn * env * EnvCode component * cleanup env demo * env * rm remark plugin * auth request context * auth req component * authorize endpoint construction * rev react page * fix endpoint * styling * query params with anchor * desc * tailwind coexistence * fix styles * add login_hint, organizationId scope * auth request without prompt * show login_hint * sync displayed url with actual href * fix fcn * coloring * Update docs/src/components/authrequest.jsx Co-authored-by: mffap <mpa@zitadel.com> * Update docs/src/components/authrequest.jsx Co-authored-by: mffap <mpa@zitadel.com> * Update docs/src/components/authrequest.jsx Co-authored-by: mffap <mpa@zitadel.com> * Update docs/src/components/authrequest.jsx Co-authored-by: mffap <mpa@zitadel.com> * Update docs/src/components/authrequest.jsx Co-authored-by: mffap <mpa@zitadel.com> * Update docs/src/components/authrequest.jsx Co-authored-by: mffap <mpa@zitadel.com> * add plausible, header * add pkce * move * adds pkce code challenge * replace cboa * reaname and move to required * fall back to cboa due to webpack error * trailing slash * reorder org_id * remove resourceowner * texts * update references * buffer, fix some react dom components * Apply suggestions from code review Co-authored-by: Florian Forster <florian@zitadel.com> * standard scopes Co-authored-by: mffap <mpa@zitadel.com> Co-authored-by: Florian Forster <florian@zitadel.com>
Do you look for a user management that's quickly set up like Auth0 and open source like Keycloak?
Do you have project that requires a multi-tenant user management with self-service for your customers?
Look no further — ZITADEL combines the ease of Auth0 with the versatility of Keycloak.
We provide you with a wide range of out of the box features to accelerate your project. Multi-tenancy with branding customization, secure login, self-service, OpenID Connect, OAuth2.x, SAML2, Passwordless with FIDO2 (including Passkeys), OTP, U2F, and an unlimited audit trail is there for you, ready to use.
With ZITADEL you can rely on a hardened and extensible turnkey solution to solve all of your authentication and authorization needs.
🏡 Website 💬 Chat 📋 Docs 🧑💻 Blog 📞 Contact
Get started
Deploy ZITADEL (Self-Hosted)
Deploying ZITADEL locally takes less than 3 minutes. So go ahead and give it a try!
See all guides here
If you are interested to get professional support for your self-hosted ZITADEL please reach out to us!
Setup ZITADEL Cloud (SaaS)
If you want to experience a hands-free ZITADEL, you should use ZITADEL Cloud.
It is free for up to 25'000 authenticated requests and provides you all the features that make ZITADEL great. Learn more about the pay-as-you-go pricing.
Why choose ZITADEL
We built ZITADEL with a complex multi-tenancy architecture in mind and provide the best solution to handle B2B customers and partners. Yet it offers everything you need for a customer identity (CIAM) use case.
- API-first approach
- Strong audit trail thanks to event sourcing as storage pattern
- Actions to react on events with custom code and extended ZITADEL for you needs
- Branding for a uniform user experience across multiple organizations
- Self-service for end-users, business customers, and administrators
- CockroachDB or a Postgres database as reliable and widespread storage option
Features
- Single Sign On (SSO)
- Passwordless with FIDO2 support (Including Passkeys)
- Username / Password
- Multifactor authentication with OTP, U2F
- Identity Brokering
- Machine-to-machine (JWT profile)
- Personal Access Tokens (PAT)
- Role Based Access Control (RBAC)
- Delegate role management to third-parties
- Self-registration including verification
- Self-service for end-users, business customers, and administrators
- OpenID Connect certified => OIDC Endpoints, OIDC Integration Guides
- SAML 2.0 => SAML Endpoints, SAML Integration Guides
- Postgres (version >= 14) or CockroachDB (version >= 22.0)
Track upcoming features on our roadmap.
Integrate your application
Quickstarts
Get started with your preferred language with our Quickstarts.
If you miss something please feel free to join the Discussion
Example applications
Clone one of our example applications or deploy them directly to Vercel.
OpenID Connect RP Libraries
Use any of the Open ID Connect certified RP implementations in your preferred language. As certified OpenID Provider, ZITADEL is compatible with any of the implementations.
Client libraries
| Language / Framework | Client | API | Machine auth (*) | Auth check (**) | Thanks to the maintainers |
|---|---|---|---|---|---|
| .NET | zitadel-net | GRPC | ✔️ | ✔️ | smartive 👑 |
| Dart | zitadel-dart | GRPC | ✔️ | ❌ | smartive 👑 |
| Elixir | zitadel_api | GRPC | ✔️ | ✔️ | jshmrtn 🙏🏻 |
| Go | zitadel-go | GRPC | ✔️ | ✔️ | ZITADEL |
| Rust | zitadel-rust | GRPC | ✔️ | ❌ | smartive 👑 |
| JVM | 🚧 WIP | ❓ | ❓ | TBD | |
| Python | 🚧 WIP | ❓ | ❓ | TBD | |
| Javascript | ❓ | ❓ | ❓ | Maybe you? |
(*) Automatically authenticate service accounts with JWT Profile.
(**) Automatically check if the access token is valid and claims match
How To Contribute
Details about how to contribute you can find in the Contribution Guide
Contributors
Made with contrib.rocks.
Showcase
Passwordless Login
Use our login widget to allow easy and secure access to your applications and enjoy all the benefits of passwordless (FIDO 2 / WebAuthN):
- works on all modern platforms, devices, and browsers
- phishing resistant alternative
- requires only one gesture by the user
- easy enrollment of the device during registration
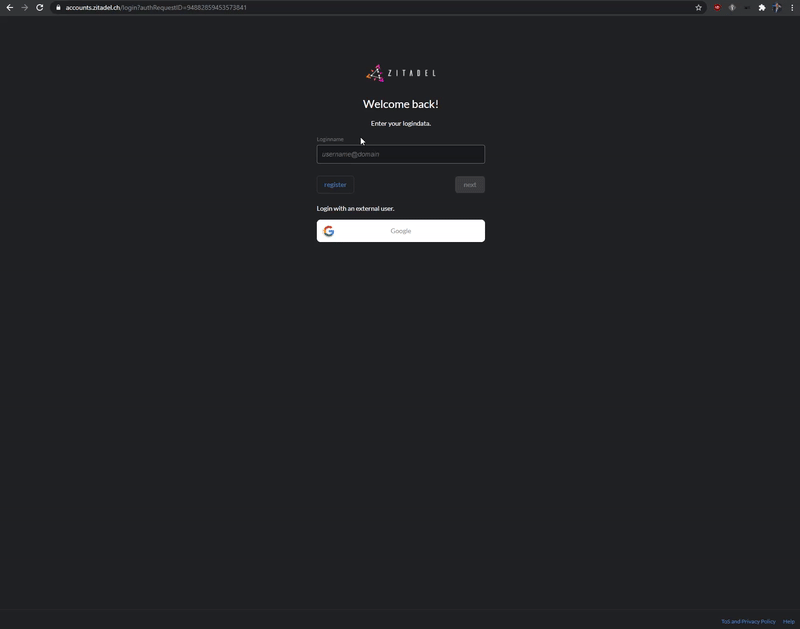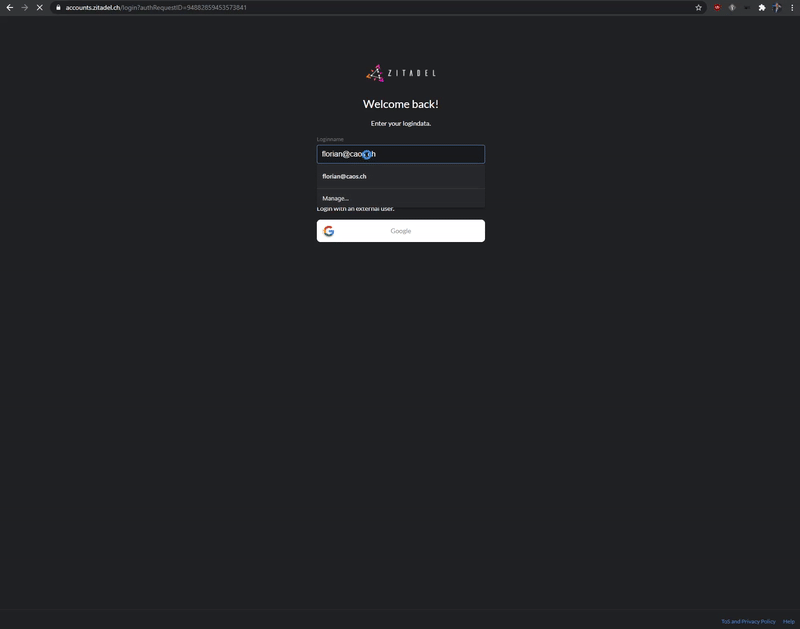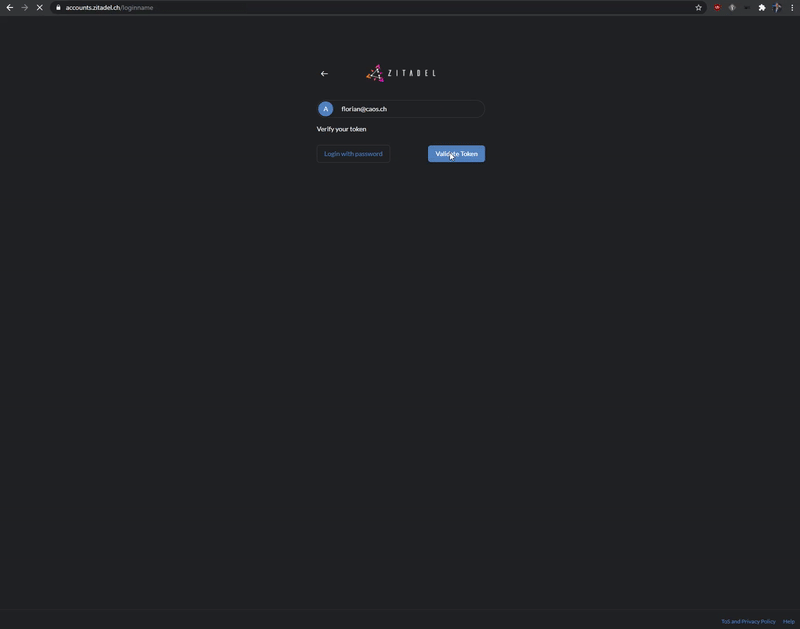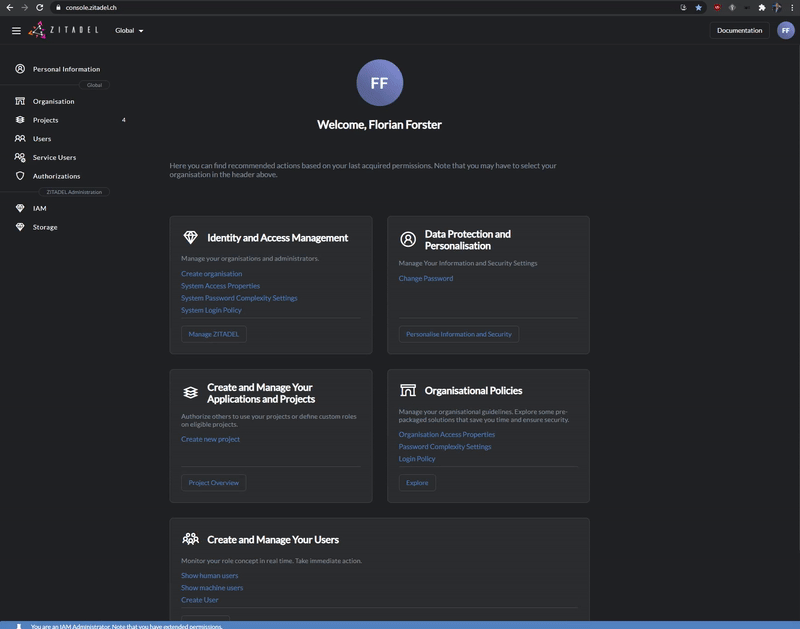
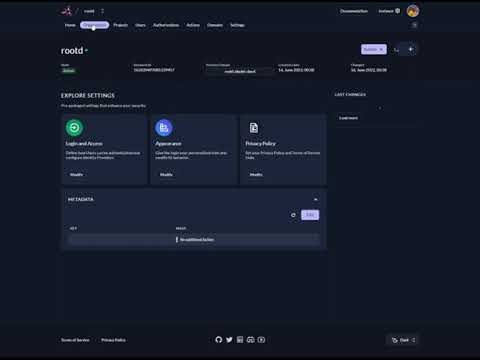
Admin Console
Use Console or our APIs to setup organizations, projects and applications.
Security
See the policy here
License
See the exact licensing terms here
Unless required by applicable law or agreed to in writing, software distributed under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. See the License for the specific language governing permissions and limitations under the License.